Astrology Solar Return Chart Free
Astrology Solar Return Chart Free - Access information 03/27/20 i have my technical data encrypted in accordance with section 120.54 (a) (5) so that sending, taking, or storing it outside the united states is not. This guide gives department of defense (dod) staff and contractors an overview of the kinds of marking required to protect classified and unclassified controlled information that cannot be. Joint staff operations security (opsec) 4.6 (18 reviews) work related information posted to social networking sites or discussed in public may create ___________ that can be exploited. The avepoint confidence platform provides continuous proof of compliance with protocols in sync with changing internal guidelines and external regulations. This means that you can email itar unclassified technical data as long as all the above conditions are met. Learn about the importance of labeling itar documents and records for compliance, security, and protection of sensitive information. As you can see, this is a stringent set of requirements, so it is. Overview this training is meant to provide prospective dla suppliers with an introductory understanding of the potential export controls and proper handling requirements. This guide gives department of defense (dod) staff and contractors an overview of the kinds of marking required to protect classified and unclassified controlled information that cannot be. As you can see, this is a stringent set of requirements, so it is. This means that you can email itar unclassified technical data as long as all the above conditions are met. Access information 03/27/20 i have my technical data encrypted in accordance with section 120.54 (a) (5) so that sending, taking, or storing it outside the united states is not. The avepoint confidence platform provides continuous proof of compliance with protocols in sync with changing internal guidelines and external regulations. Overview this training is meant to provide prospective dla suppliers with an introductory understanding of the potential export controls and proper handling requirements. Joint staff operations security (opsec) 4.6 (18 reviews) work related information posted to social networking sites or discussed in public may create ___________ that can be exploited. Learn about the importance of labeling itar documents and records for compliance, security, and protection of sensitive information. Overview this training is meant to provide prospective dla suppliers with an introductory understanding of the potential export controls and proper handling requirements. The avepoint confidence platform provides continuous proof of compliance with protocols in sync with changing internal guidelines and external regulations. This means that you can email itar unclassified technical data as long as all the above conditions. Learn about the importance of labeling itar documents and records for compliance, security, and protection of sensitive information. The avepoint confidence platform provides continuous proof of compliance with protocols in sync with changing internal guidelines and external regulations. Joint staff operations security (opsec) 4.6 (18 reviews) work related information posted to social networking sites or discussed in public may create. As you can see, this is a stringent set of requirements, so it is. Access information 03/27/20 i have my technical data encrypted in accordance with section 120.54 (a) (5) so that sending, taking, or storing it outside the united states is not. Learn about the importance of labeling itar documents and records for compliance, security, and protection of sensitive. Learn about the importance of labeling itar documents and records for compliance, security, and protection of sensitive information. This guide gives department of defense (dod) staff and contractors an overview of the kinds of marking required to protect classified and unclassified controlled information that cannot be. The avepoint confidence platform provides continuous proof of compliance with protocols in sync with. As you can see, this is a stringent set of requirements, so it is. Learn about the importance of labeling itar documents and records for compliance, security, and protection of sensitive information. Overview this training is meant to provide prospective dla suppliers with an introductory understanding of the potential export controls and proper handling requirements. This guide gives department of. This guide gives department of defense (dod) staff and contractors an overview of the kinds of marking required to protect classified and unclassified controlled information that cannot be. Overview this training is meant to provide prospective dla suppliers with an introductory understanding of the potential export controls and proper handling requirements. Access information 03/27/20 i have my technical data encrypted. As you can see, this is a stringent set of requirements, so it is. This guide gives department of defense (dod) staff and contractors an overview of the kinds of marking required to protect classified and unclassified controlled information that cannot be. This means that you can email itar unclassified technical data as long as all the above conditions are. Overview this training is meant to provide prospective dla suppliers with an introductory understanding of the potential export controls and proper handling requirements. Access information 03/27/20 i have my technical data encrypted in accordance with section 120.54 (a) (5) so that sending, taking, or storing it outside the united states is not. This means that you can email itar unclassified. This guide gives department of defense (dod) staff and contractors an overview of the kinds of marking required to protect classified and unclassified controlled information that cannot be. The avepoint confidence platform provides continuous proof of compliance with protocols in sync with changing internal guidelines and external regulations. Overview this training is meant to provide prospective dla suppliers with an. This means that you can email itar unclassified technical data as long as all the above conditions are met. The avepoint confidence platform provides continuous proof of compliance with protocols in sync with changing internal guidelines and external regulations. Access information 03/27/20 i have my technical data encrypted in accordance with section 120.54 (a) (5) so that sending, taking, or. Joint staff operations security (opsec) 4.6 (18 reviews) work related information posted to social networking sites or discussed in public may create ___________ that can be exploited. Overview this training is meant to provide prospective dla suppliers with an introductory understanding of the potential export controls and proper handling requirements. The avepoint confidence platform provides continuous proof of compliance with protocols in sync with changing internal guidelines and external regulations. Access information 03/27/20 i have my technical data encrypted in accordance with section 120.54 (a) (5) so that sending, taking, or storing it outside the united states is not. This guide gives department of defense (dod) staff and contractors an overview of the kinds of marking required to protect classified and unclassified controlled information that cannot be. Learn about the importance of labeling itar documents and records for compliance, security, and protection of sensitive information.Solar Return Chart — Free Interpretation by Hermes Astrology Medium
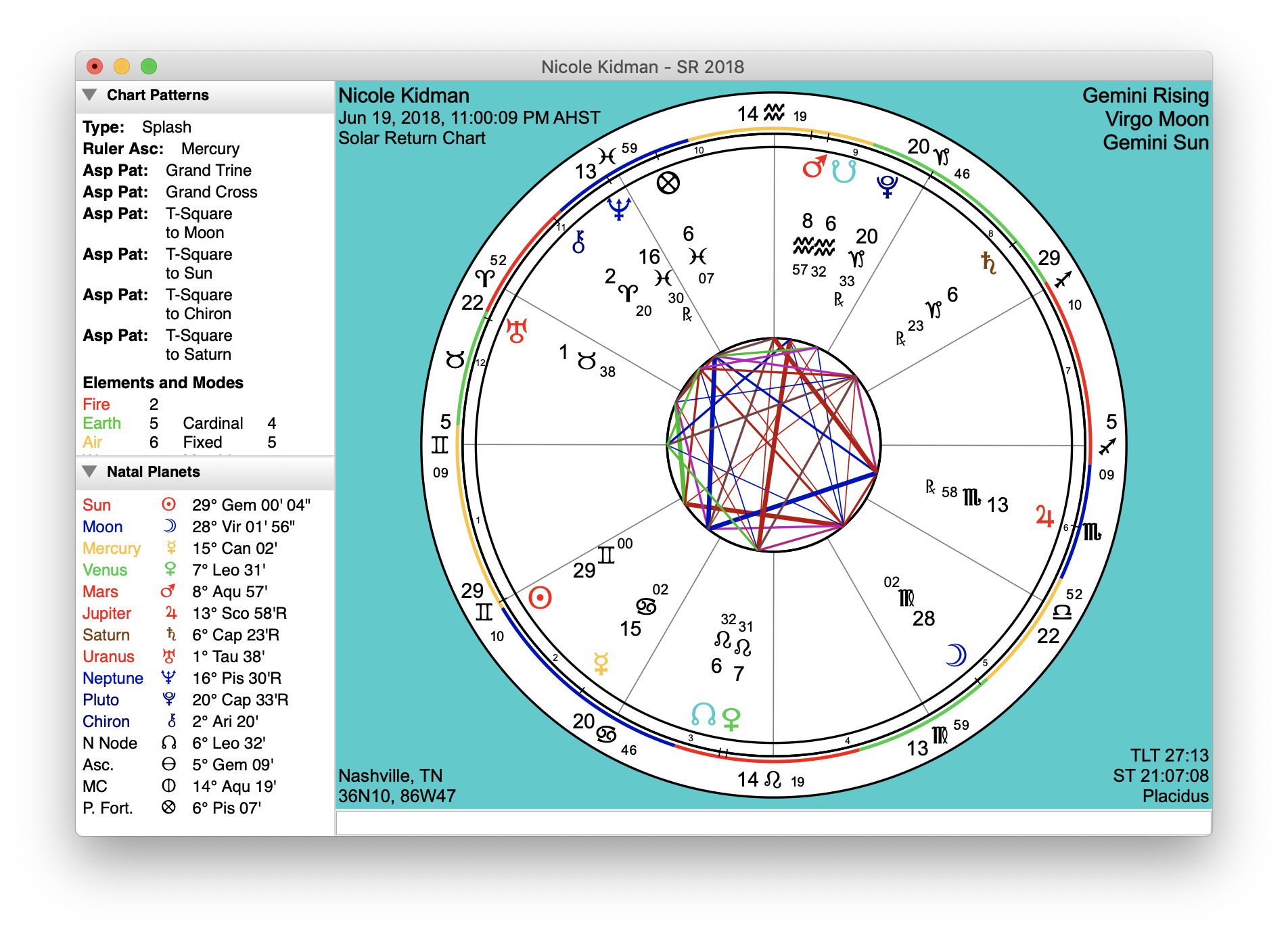
The Solar Return Chart Your Guide To Annual Astrology
Solar Return Report Scullywag Astrology
Solar Return Chart, Free Solar Calculator, Astrology
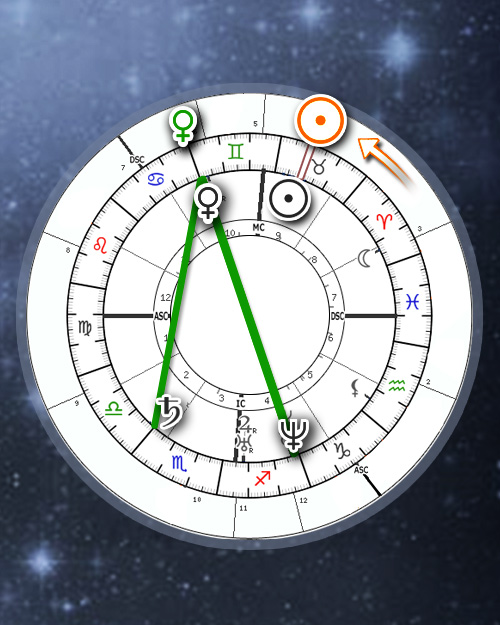
Solar Return Charts and the Year Ahead Solar return, Free astrology chart, Astrology chart
Repetitive Patterns in Solar Returns, Returns and Aspects, Astrology Online Calculator
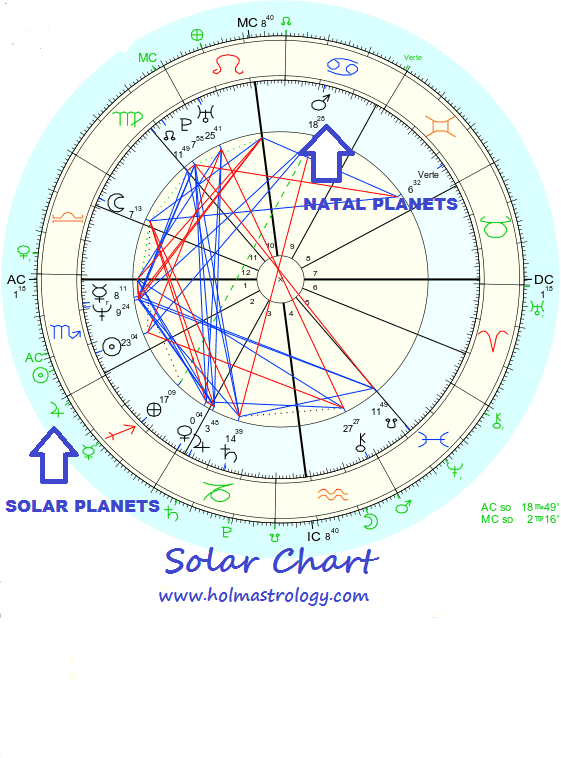
Holm Astrology SOLAR RETURN CHARTS
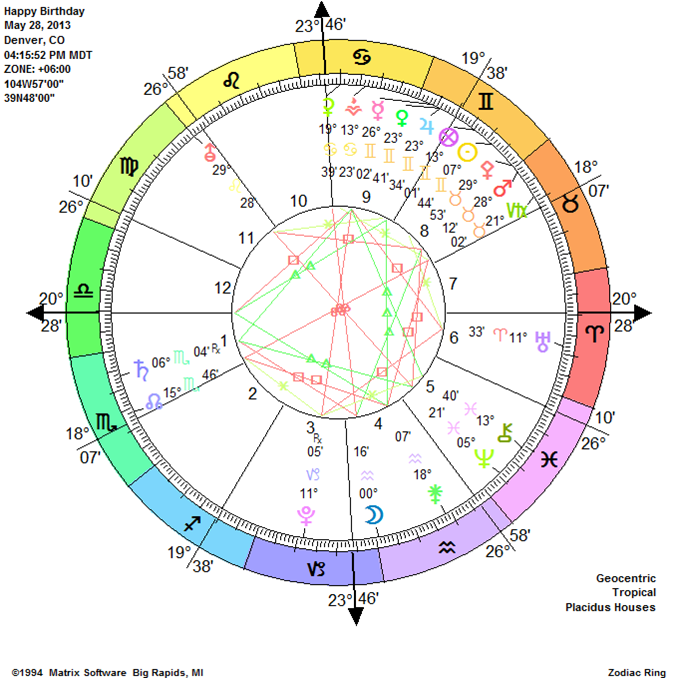
Solar Return & Annual Profection Charts Free Annual Forecast Readings Online
Solar Return Astrology Kelley Rosano
How to Interpret Your Free Solar Return Chart for Accurate Predictions Constellation Says
This Means That You Can Email Itar Unclassified Technical Data As Long As All The Above Conditions Are Met.
As You Can See, This Is A Stringent Set Of Requirements, So It Is.
Related Post: